Enterprise Attacker Emulation and C2 Implant Development w/ Joff Thyer
In May 2021, I had the pleasure of sitting in the virtual iteration of Wild West Hacking Fest’s training offering written and taught by Joff Thyer called Enterprise Attacker Emulation and C2 Implant Development
To save time here is the link to the course: Enterprise Attacker Emulation and C2 Implant Development w/ Joff Thyer
The breakdown of the course content goes like this:
- Module 1: Commodity C2 Frameworks
- Module 2: The Defense Landscape
- Module 3: Threat Modeling and Attacker Emulation
- Module 4: Anatomy of a C2 Channel
- Module 5: Open C2 RAT Framework
- Module 6: Your own C#/.NET Implant
- Module 7: Living off The Land
- Module 8: Python OpenC2Rat Implant
- Module 9: Shellcode Execution with Python
- Module 10: Shellcode Execution with GOLang
- Module 11: GOLang and .NET
- Module 12: Shellcode Execution with C#
- Module 13: Wrapping up and Future Directions
BLUF (Bottom Line Up Front)
If the course description peeks your interest, TAKE THE COURSE.
I really debated doing a comprehensive write-up and assessment of course however, the more I thought about it just did not make sense.
Why you might ask?
Glad you did.
Well…frankly, because if anyone reading this post has any interest in the topics outlined above, should just take the course. That is my honest assessment.
The cost of this course was $495 but as I told Joff during the training, I feel the Content per $ value of his course far exceeds any other offering I have taken in recent years by a massive margin.
The materials in this course are fresh and relevant. In some cases it was real time, in that changes needed to be made on the fly to bypass detections that previously were not triggering. The real time need to modify code really highlighted ever-changing landscape that is offensive tooling, and presented a very real world scenario.
It was abundantly clear that Joff had poured immense amount of time and effort building this course and the content provided to the students was off the chart. To start, you receive code to a completely custom C2 framework that was created purposely for this course, an entire framework…nice.
The sheer amount of code that comes included with course is pretty impressive. I cannot really imagine just how much time went into the development of the code and that alone makes the price of admission a complete steal. Not only are students provided access to the code repos for the course but Joff is gracious enough to provide students with keys to be able to pull the latest versions of the code for a period of 180 days, post taking the course. This means as he continues to refine the content, students that have recently taken the course can benefit from those refinements. Again this is value that keeps going beyond the timeline of the course.
In terms of the content, a lot of the concepts were not new for me in the least but having it in the context of a completely new C2 framework was great.
I took a lot away from the course that I have been able to leverage in my day job but none more valuable to me was the use of pre- / post-build events in Visual Studio. Not being a programmer and only recently starting to develop some dotNet tooling, pre- / post-build events were not something I had ever used or frankly new about. Since learning about them, it painfully obvious that they would exist but who knew?!?! Not me. Having the ability to modify my code at compilation time with techniques such as encoding, encrypting, and other obfuscation processes automatically is a game changer for myself. I was already doing all of this, but it was a manual process and frankly could be error-prone.
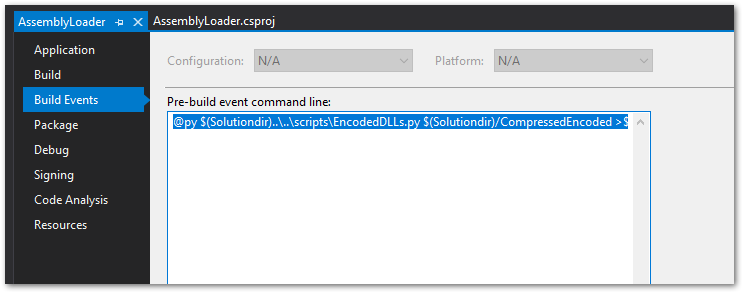
I am a fan of automation where ever possible and this has been the golden ticket for me. Despite all the work and code that went into this course, it was this little nugget that helped me the most. This will be a tool in my arsenal moving forward for sure.
TL/DR
The Enterprise Attacker Emulation and C2 Implant Development w/ Joff Thyer was great, and I could not recommend it more.